Digital Warfare Intensifies: Inside the Hacktivist Offensive in the Israel-Iran Conflict
Over the weekend, the simmering geopolitical tension between Israel and Iran erupted in cyberspace. What began as isolated hacktivist activity has escalated into a full-scale digital battle, with nearly 100 hacktivist groups launching attacks aligned with physical hostilities.
This fast-evolving cyber dimension illustrates the growing power of decentralized digital actors. Cyber warfare has become a vital front in modern conflict — a battleground shaped by propaganda, disruption, and psychological pressure.
Hacktivist Landscape: Skewed and Expanding
IntelHawk threat intelligence monitoring has recorded an asymmetric mobilization of cyber groups:
-
65 pro-Iranian groups
-
11 anti-Iranian groups
-
6 pro-Israeli groups
-
15+ unaffiliated or opportunistic groups
Many of these actors are coordinating in real-time via Telegram, dark web forums, and open-source social media, adapting tactics as the situation develops.
Key Hacktivist Attacks and Tactics
Pro-Iranian Attacks
1. Massive DDoS Campaigns
-
Targets: Israeli government, financial institutions, telecoms, and logistics
-
Tactics: Botnets launched volumetric DDoS attacks, with some outages reported in public infrastructure
2. Website Defacements
-
Government and private sector websites were defaced with political messages, often accompanied by videos, Islamic symbolism, and anti-Israel slogans
3. Data Breaches & Leak Threats
-
Several pro-Iranian groups claimed to exfiltrate Israeli citizen data and threatened public leaks
-
Samples shared on Telegram showed identity records and partial credentials
4. Cyber espionage and Social Engineering
-
Targeted Phishing (Spear Phishing): Custom-crafted emails or messages to infiltrate specific individuals (e.g., military, diplomats, researchers).
-
Job Lures (as seen in the Telegram screenshot): Fake employment offers used to recruit or exploit insiders.
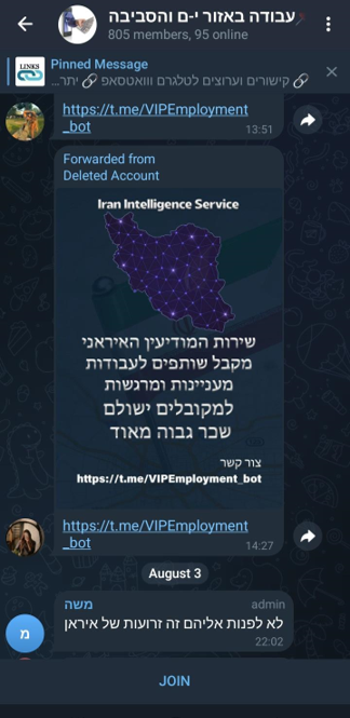
cyber espionage or social engineering attempt disguised as job recruitment. It aims to lure individuals, potentially for intelligence gathering or access to sensitive systems. Common in state-aligned disinformation and HUMINT (human intelligence) campaigns.
Anti-Iranian and Pro-Israeli Cyber Responses
1. Attacks on Iranian Infrastructure
-
Alleged intrusions into local grid networks and public-facing government portals
-
Temporary blackouts and surveillance camera disruptions reported in limited areas
2. Leaks of Internal Iranian Emails
-
Hacktivist groups published communications from state-affiliated media and clerical bodies, aimed at exposing disinformation practices
3. Counter-DDoS and Botnet Takedowns
-
Anti-Iranian cyber collectives retaliated by targeting pro-Iranian infrastructure and Telegram-based C2 channels

Overview of Israel and Iran Cyber Capabilities
Third-Party & Opportunistic Hacktivism
1. Propaganda Ransomware
-
Politically motivated ransomware deployed without ransom demands; instead, victims received ideological statements (e.g., “Free Palestine”)
2. False-Flag Tactics
-
IntelHawk detected coordinated attempts to spoof attribution by mimicking opposing group tactics — creating confusion around attack origins
Cyberattacks against Israel surged by 700% in the two days following June 12, compared to the period before, Jerusalem Post reported. Hacker groups took position, prepared, and swiftly executed their attacks.

Tactical Analysis: IntelHawk Observations
IntelHawk has tracked and categorized evolving threat tactics based on real-time intelligence:
| Tactic | Observed Use |
|---|---|
| Telegram Coordination | Group operations and live targeting decisions made on encrypted messaging platforms |
| Low-Sophistication Attacks | Widespread use of DDoS and defacements to generate publicity quickly |
| Dark Web Chatter | Data auctions, toolkits, and service offers spiked on forums tied to cyber campaigns |
| Psychological Warfare | Attacks timed to coincide with public fear and military escalations, amplifying impact |
| Tool Sharing and Collaboration | Emerging alliances between hacktivist collectives boost campaign effectiveness |
In Conclusion
In fast-moving conflicts, the cyber dimension can be a precursor or multiplier of physical action. While not every attack delivers technical damage, the strategic and psychological impacts are undeniable.
The Israel-Iran cyber confrontation has already demonstrated how non-state actors can destabilize digital environments and accelerate tension. With dozens of hacktivist groups now fully engaged, the situation remains volatile — and likely to intensify.
IntelHawk ensures you’re prepared for the latest cyber threats.
With full-spectrum coverage across surface, deep, and dark web channels, IntelHawk delivers the visibility and context needed to understand, assess, and act on threats as they evolve.
IntelHawk Cyber Threat Intelligence
-
Real-time monitoring of threat actors, IOCs, and malware behavior
-
Correlates geopolitical events with active cyber campaigns targeting your sector or region
Social Media & Telegram Surveillance
-
Tracks group announcements, target lists, and attack coordination across Telegram, Discord, and X (formerly Twitter)
-
Detects fast-moving disinformation or reputational threats
Dark Web Monitoring
-
Watches closed forums, ransomware marketplaces, and leak sites for brand mentions, credential dumps, and targeted campaign discussions
Vulnerability & Attack Surface Tracking
-
Maps exposed services and infrastructure tied to active CVEs
-
Connects vulnerabilities with current threat group TTPs for prioritized patching
Automated Threat Rule Generation
-
Converts threat intel into YARA/Sigma rules, alerts, and integration-ready content for SIEM/XDR platforms
-
Enables rapid defensive configuration and real-time SOC response
IntelHawk Link Analysis: Uncovering Threat Infrastructure in Real Time
IntelHawk’s graph-based link analysis system offers a powerful lens into the interconnected layers of threat actor infrastructure — from dark web posts to exposed credentials and IP pivots.
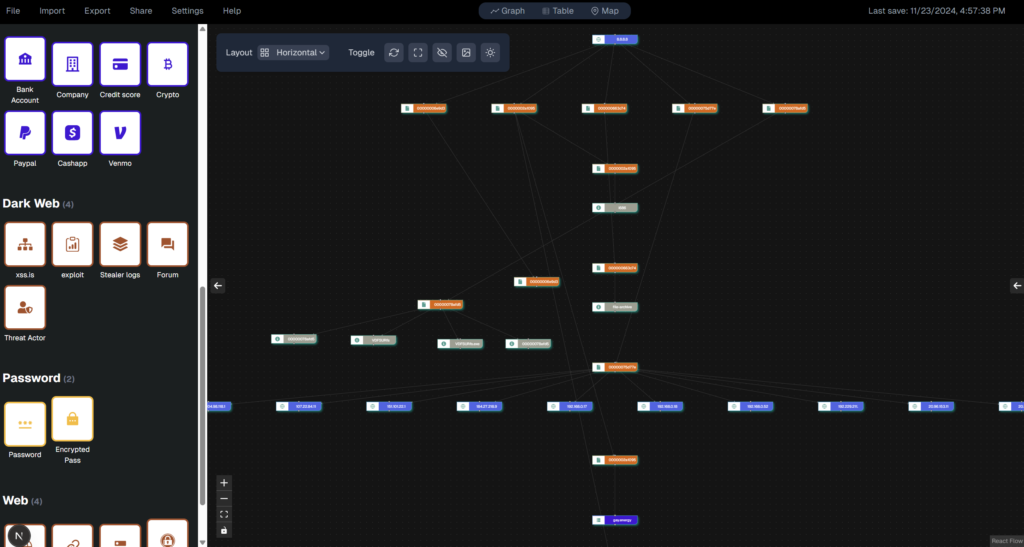
What This Graph Shows:
-
Dark Web Entities (orange nodes) tied to:
-
Dark web forums (e.g., xss.is, exploit packs)
-
Stealer logs containing exfiltrated data
-
-
Indicators of Compromise (IOCs):
-
File hashes, encrypted archives, IPs, C2 servers and malware builds
-
Infected hosts (blue nodes) traced back to exposed IPs
-
-
Infrastructure Links:
-
Identifies reuse of IPs, usernames, hashes or login panels across multiple campaigns
-
IntelHawk users can pivot between Graph, Table, and Map views in real-time and export threat paths for incident response teams.
Key Use Cases:
-
Attribution Building – Correlate usernames, payload hashes, and infrastructure back to a known group or persona.
-
Early Detection – Discover new IPs or credentials being circulated for future campaigns.
-
Attack Surface Reduction – Identify your own assets appearing in stealer logs or credential dumps.
IntelHawk users can pivot between Graph, Table, and Map views in real-time and export threat paths for incident response teams.
Real-Time Threat Intelligence at Work: IntelHawk Dashboard Snapshot
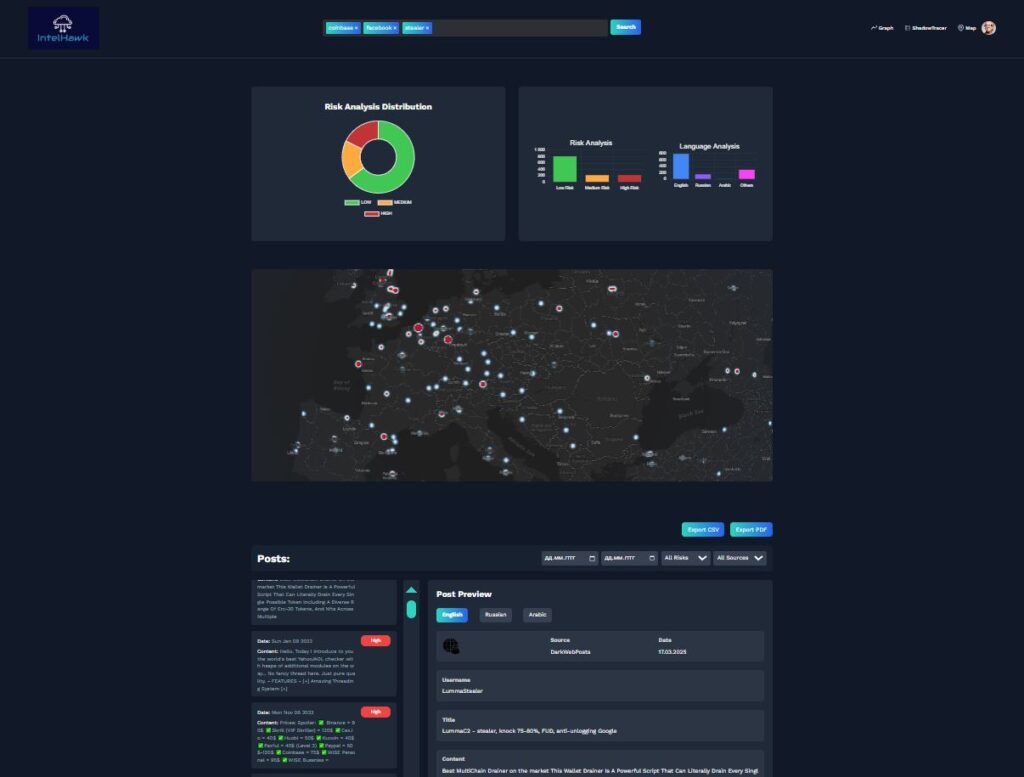
In moments of escalating geopolitical cyber activity — like the recent Israel-Iran conflict — real-time visibility is everything.
Below is a snapshot from the IntelHawk Threat Intelligence Platform, providing a live overview of:
-
Risk Distribution across low, medium, and high-level threats
-
Geo-targeted Attacks mapped in real time
-
Language and Source Analysis of threat actor communications
-
Dark Web Posts with high-risk indicators and malicious tool promotions
Above: IntelHawk dashboard showing risk levels, language patterns, and geo-located cyber activity. Data pulled from Dark Web forums, Telegram, and open-source cyber signals.
💡 While this preview is compressed for web, a full-resolution export with actionable filters (date, source, severity) is available to IntelHawk platform users in PDF or CSV formats.
Stay ahead of the threat — get continuous updates and insights





