Aeroflot Suffers Catastrophic Cyberattack: Complete Infrastructure Compromise by Silent Crow
Hacktivist group destroys over 7,000 virtual machines after maintaining 12-month persistent access to Russian airline’s critical systems
Executive Summary
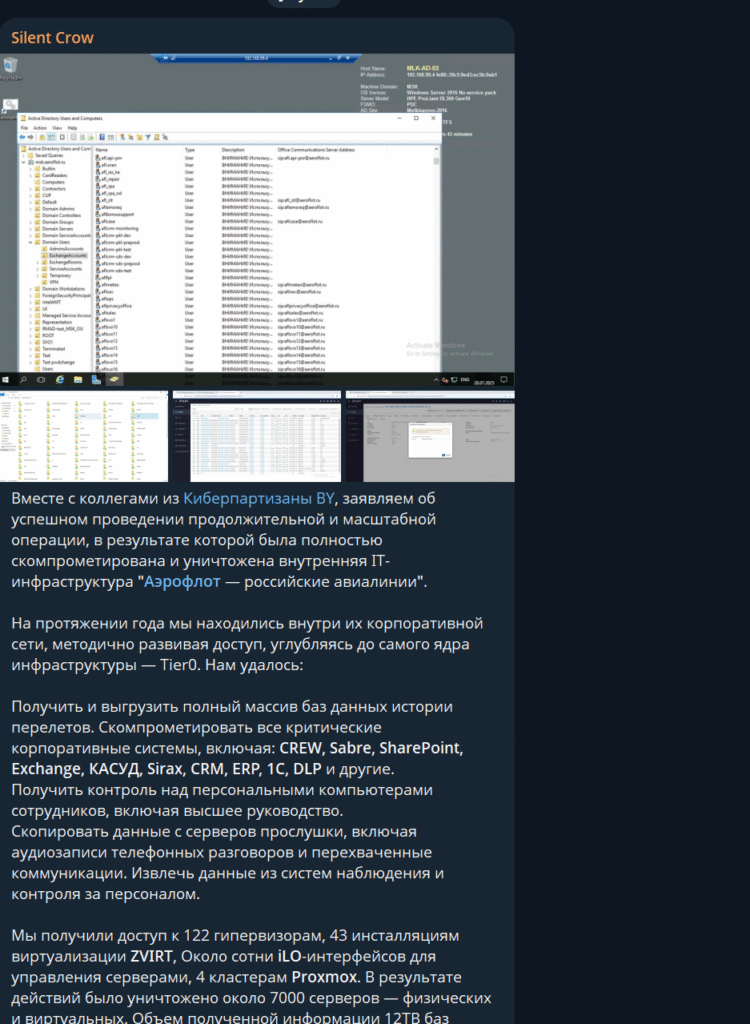
On July 28, 2025, Russian national airline Aeroflot experienced one of the most devastating cyberattacks in aviation industry history. The attack, attributed to the hacktivist group “Silent Crow”—believed to be associated with pro-Ukrainian cyber networks and Belarusian cyber-activists—resulted in the systematic destruction of over 7,000 virtual machines, database hosts, and backup systems.
The sophistication and scope of this attack distinguish it from typical ransomware operations. Evidence suggests the attackers maintained privileged access to Aeroflot’s core infrastructure for over twelve months, conducting extensive reconnaissance before executing coordinated destruction across the airline’s digital ecosystem.
This represents a complete Active Directory compromise executed with surgical precision and demonstrates advanced understanding of enterprise network architecture.
Technical Analysis: Evidence of Total Infrastructure Control
Leaked screenshots distributed through Telegram channels and dark web forums provide unprecedented insight into the attack methodology and scope of compromise:
Active Directory Domain Compromise
Forensic evidence reveals complete administrative access to Aeroflot’s Active Directory environment within the msk.aeroflot.ru domain. Screenshots demonstrate unrestricted access to:
- Hundreds of user accounts including service accounts and administrative roles
- Exchange server infrastructure and associated communications systems
- Office Communications Server and SIP address configurations
- Complete organizational unit structure and security group memberships
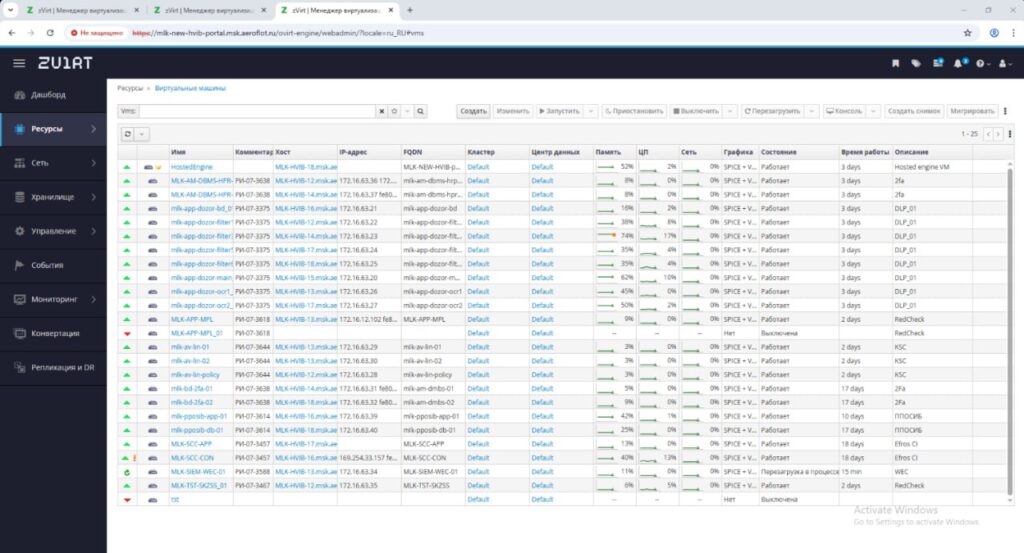
The exposure of internal usernames and communication addresses indicates significant information security hygiene failures and represents a substantial intelligence gathering opportunity for threat actors.
File System and Network Share Access
Documentation shows comprehensive access to Aeroflot’s internal file sharing infrastructure (172.16.170.112), including business-critical directories:
Revenue_Optimizer– Revenue management systemsHourly_Booking_Intake– Real-time booking dataCommercial_Analytics– Business intelligence and analyticsOracleBI_sistema_otchetnosti– Enterprise reporting systems
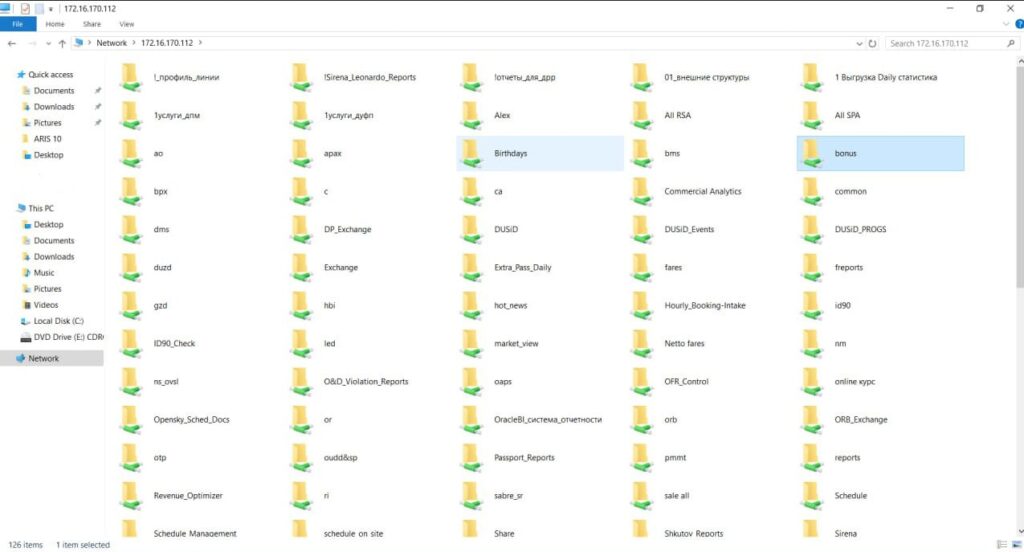
This level of access suggests flat network architecture with insufficient segmentation between application tiers, file storage, and database systems.
Virtualization Infrastructure Control
Perhaps most concerning is documented access to Aeroflot’s virtualization management platform. Screenshots show administrative control of zVirt (Russian-localized oVirt/RHEV), providing complete visibility into:
- Virtual machine inventory and resource allocation
- Network topology and IP address schemas
- Storage cluster configuration and capacity metrics
- Critical business system hostnames and operational status
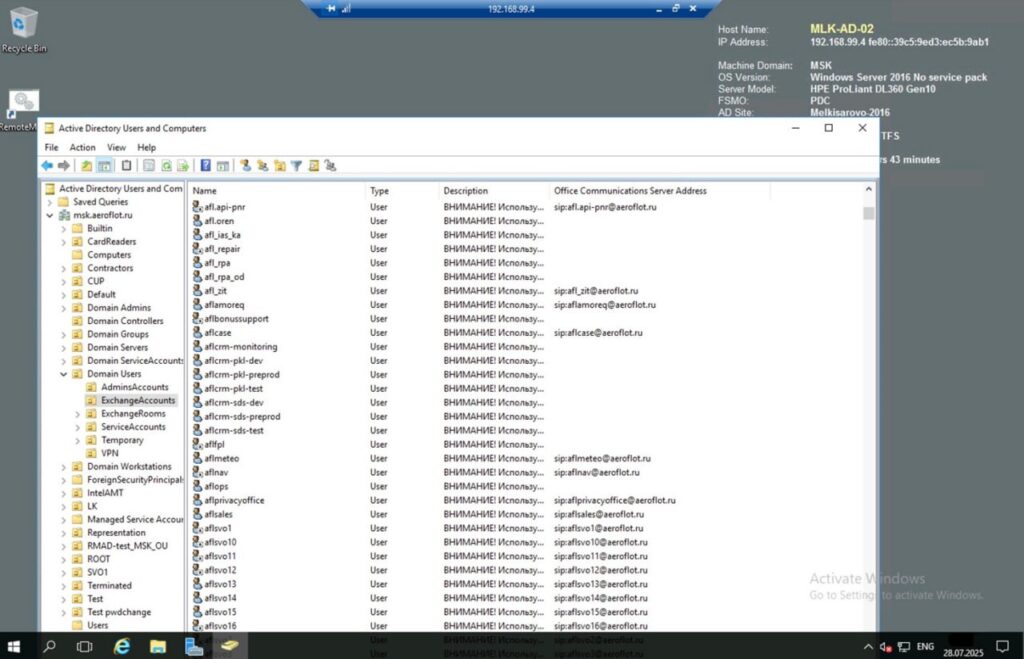
Control of the virtualization layer represents the highest level of infrastructure compromise, enabling attackers to manipulate, monitor, or destroy any system within the environment.
Operational Destruction Phase
In the final phase of the attack, threat actors demonstrated their control by systematically shutting down production systems through the hypervisor management interface. Evidence shows the deliberate shutdown of critical Data Loss Prevention (DLP) servers, with attackers leaving digital signatures in system shutdown logs.
The absence of technical controls preventing unauthorized system shutdowns through administrative interfaces represents a fundamental failure in privileged access management.
Threat Actor Profile: Silent Crow
Silent Crow operates through the Telegram channel @silentcrow_reborn and has previously claimed responsibility for attacks against Russian logistics and telecommunications infrastructure. Intelligence analysis indicates:
- Operational collaboration with CyberPartisans (Belarus) and Ukrainian cyber warfare units
- Historical involvement in HermeticWiper and FoxBlade operations
- Primary motivation appears to be information warfare rather than financial gain
- Strategic objective of undermining confidence in Russian state-operated digital infrastructure
This attack represents intentional digital sabotage designed to inflict maximum operational disruption rather than traditional cybercriminal monetization.
Root Cause Analysis
The successful compromise of Aeroflot’s infrastructure resulted from multiple interconnected security architecture failures:
Identity and Access Management Failures
- Flat Active Directory architecture without administrative tier separation
- Excessive service account privileges including domain administrative rights
- Shared credential usage across multiple systems and services
- Lack of privileged access management controls
Network Architecture Vulnerabilities
- Insufficient network segmentation between critical system tiers
- Absence of east-west traffic inspection and filtering
- Direct connectivity between user workstations and backend infrastructure
- Lack of zero-trust network architecture implementation
Business Continuity and Recovery Deficiencies
- Backup systems accessible through compromised domain credentials
- Absence of immutable backup storage solutions
- Insufficient air-gapped recovery infrastructure
- Lack of tested disaster recovery procedures
Protect Your Organization from Advanced Persistent Threats
With scams and cybercrime going through the roof, you need to stay protected. Book a free demo with us and find out how IntelHawk can help safeguard you and your organization against costly data breaches.
See A Free demo





