Updated: July 2025 | IntelHawk OSINT REPORT
Summary
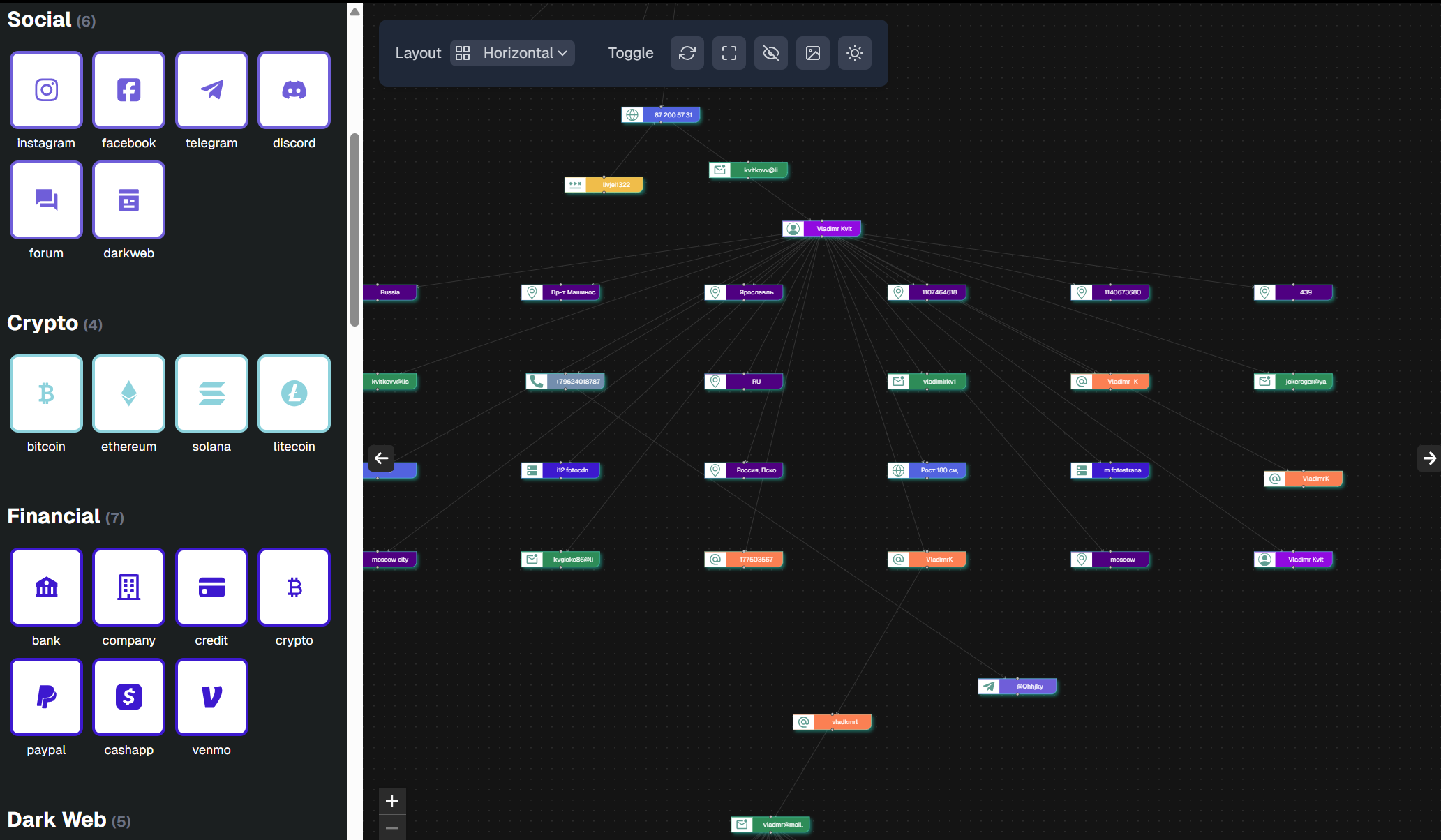
IntelHawk has confirmed and expanded the profile of Vladimir Viktorovich Kvitko, connecting his verified government identity with historical Telegram aliases, Russian cybercrime forum registrations, and international travel patterns.
Most notably, Kvitko is believed to be the individual operating under the alias “Professor”, a central figure in the Conti ransomware group, responsible for infrastructure management, offline coordination, and financial operations…
Vladimir Kvitko is registered and resides in Moscow. However, he was present in the Altai Republic from June 15, 2021, to June 17, 2021.
Confirmed Identity
Full Name: Vladimir Viktorovich Kvitko
Date of Birth: October 23, 1984
Passport Number: 4509 506672
Registered Address: Ulitsa Krasnoarmeyskaya, Building 10, Apt. 55, Moscow, Russia
SNILS: 142-135-202 00
T562KA97: Toyota Corolla
Company: LLC “Management Company RosRail”
Contact Information
Extensive cross-border travel to UAE, Austria, Iran, Cuba
Email: kvitkovv84@list.ru, kvitkovv@list.ru, vladimirkvitko83@gmail.com, kvitkovv00@mail.ru
Phone: +7 903 554 3030, 7 926-923-0963, 7 903-554-3030
Social Media: https://vk.com/id3851747
Wife: Ksenia Andreevna Kvitko
Telegram Activity and Historical Usernames
@Qhhjky
@MVKvitko
@ProfSD
@VladimrK
Timeline Correlation: Jabber Inactivity and Travel
June 14, 2021: “Decrypt the file, please, for the people.”
June 14–18: Silence on Jabber
June 18: “I’ll be available in a couple of hours. On the road.”
Travel Match: Altai Republic, Ust-Koksa Village, June 15–17, 2021
The absence from Jabber aligns precisely with real-world travel records, strongly reinforcing that Kvitko and “Professor” are the same person.
Role in the Conti Ransomware Group
Logistics for Conti ops (Dubai, Russia)
Shell company management
Carding ops (Cuba, India)
Decrypting Files
Money laundering (UAE, Iran)
IP & Forum Attribution
IP 87.200.57.31 was used to register on multiple russian cybercrime forums and was also used to register on a russian streaming platform called Start.ru (registered with kvitkovv@list.ru) These links further confirm that Professor and Kvitko are the same person.
Border Crossings (Source: Granitza (leaked FSB Border Control System)
Earlier trips to Cuba, Iran, and Armenia coincide with documented periods of offshore laundering and infrastructure setup. Visa cycling in Austria and the Netherlands was also used to maintain his UAE residency.
Direction | Country | City | Date | Flight | Passport |
|---|---|---|---|---|---|
To | UAE | Dubai | 05.08.2022 | EK-132 | 759207109 |
From | UAE | Dubai | 24.05.2022 | EK-131 | 759207109 |
To | Austria | Vienna | 04.09.2021 | SU-2356 | 759636455 |
From | Austria | Vienna | 17.09.2021 | SU-2185 | 759636455 |
Final Identity Overview
Full Name | Vladimir Viktorovich Kvitko |
|---|---|
DOB | 23.10.1984 |
Passport | 4509 506672 |
SNILS | 142-135-202 03 |
Address | Moscow, Russia |
Phone | +7 903 554 3030 , +7 926-923-0963 |
kvitkovv84@list.ru,kvitkovv@list.ru | |
Telegram | @Qhhjky, @ProfSD, @VladimrK |
IP | 87.200.57.31 |
Forum Use | Cybercrime forums |
Role | Logistics, offline ops |
Last Seen | UAE, Austria |
IntelHawk Assessment
Cyber infrastructure overlaps with real-world IDs
Jabber inactivity synced with travel
Repeated use of same emails, phones, IPs
Telegram handle tied to phone numbers
Ready to See IntelHawk In Action?
IntelHawk helps investigators, analysts, and cyber threat teams quickly map out threat actors’ infrastructure and generate detection rules in real time.
Attribute threat actors
Trace malicious infrastructure
Cross-link identities across hundreds of data points
Generate detection rules in real time





